To ensure SQL Server Service Packs are applied correctly and the impact of their application is minimized for both end users and your business, it’s important you know about and can implement SQL Server patching best practices and SQL Server cluster patching best practices.
This guide can help businesses implement SQL Server patching best practices to help ensure minimal downtime and disruption. In addition to outlining SQL Server patching best practices and SQL Server cluster patching best practices, I’ve also explained why SQL Server patching is so challenging and the risks associated with leaving your SQL Server unpatched.
One of the most effective ways of keeping your SQL Server patched appropriately is to automate SQL Server patching with dedicated patch management tools. For this purpose, I highly recommend SolarWinds® Patch Manager. This tool provides enterprise-grade SQL Server patching automation, with support for MySQL security patches, to keep your SQL Server up to date by simplifying the patch management process from start to finish. A 30-day free trial of Patch Manager is available here.
Why Is SQL Server Patching So Hard?
Whether we’re updating SQL Server, Microsoft SQL Server, MySQL security patches, Windows, or any other hardware, updates and patches are part of everyday life for administrators and IT professionals. Even as individuals, we often find ourselves being prompted to install an update on our personal devices. Ensuring our hardware, operating systems, and programs are appropriately patched and updated is a crucial part of maintaining supportability, performance, stability, and security.
Unfortunately, patching often requires downtime, and in some cases, a flawed patch can be the cause of issues in your infrastructure. Because of this, many admins are rightfully anxious about patching and may even postpone important updates or put them off indefinitely.
Without the help of SQL Server patching automation software, admins are faced with the following considerations when patches need to be made:
- Which servers do you consider to be mission-critical 24/7?
- Which servers may only go offline during certain timeframes?
- Which servers are subject to important dependencies?
- Which servers include vendor applications that require a certain hotfix that might not be featured in the update you mean to apply?
- Which servers currently have sp_configure changes pending and will catch you off-guard when you reboot?
These considerations make it difficult to implement multiple patches simultaneously and can be time-consuming to research. Moreover, if an administrator fails to recognize a potential obstacle or issue in advance of patch implementation, this can lead to unnecessarily lengthy downtime and disruption.
There are also hardware and Windows considerations to account for, such as:
- Do you have knowledge of when patches and updates will occur? Are you prepared?
- Do you have knowledge of which components or systems will be impacted?
- Is a SQL Server outage required?

Risks of an Unpatched SQL Server
Applying a SQL Server patch can potentially corrupt data, or even cause a database server outage. Because of this, many database administrators are hesitant to install a patch. However, the risks associated with unpatched software aren’t just inconvenient, but disastrous. When software is left unpatched, your infrastructure and systems are vulnerable to attack.
Unfortunately, many network administrators and database administrators simply aren’t aware of the vulnerabilities created by unpatched software and how they can be exploited by an insider you thought you could trust. This applies to SQL Server, Windows OS, and other software being run on the host (for example, a backup program, IIS, and VNC). You may have heard claims that even if serious SQL Server vulnerabilities were to arise, it would be unlikely anyone on the network would know how to exploit them. While this may be true, it only takes one trusted insider downloading free tools from the internet, experimenting with them, then leveraging them to access the database system to lead to serious consequences for your business. This isn’t a risk any company should take.
There are several known vulnerabilities for SQL Servers. Although patches are available for these vulnerabilities, if you were to leave your SQL Server unpatched, you would expose yourself to unnecessary risk. For example, several SQL Server weaknesses can be easily exploited if someone with malicious intentions were to use Metasploit or other commercial alternatives. As such, anyone with a standard network connection would be able to gain complete admin-level access to your SQL Server. It wouldn’t even be necessary for them to have a SQL Server or Windows login—just physical network access.
There are further opportunities for cybercriminals to gain access to your SQL server, such as exploiting unpatched programs running on the system. They might also use vulnerability scanning programs, which can assist individuals with malicious intent in identifying SQL Server-specific exploits, like denial of service, system table access, and privilege escalation. All these risks can be avoided if patches are applied when recommended. Remember an external firewall can’t prevent these internal risks.
The risk of a botched patch installation has become increasingly minimal, but the consequences of unpatched software can be devastating for a business. Administrators should never shy away from installing recommended patches.
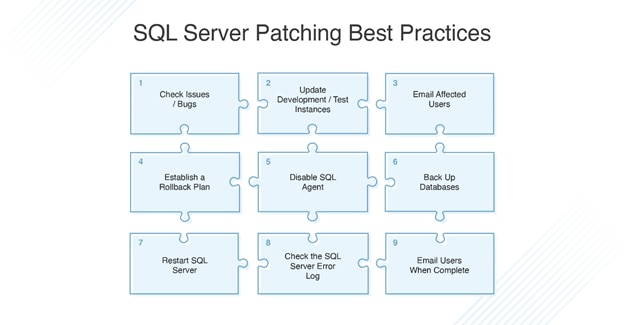
SQL Server Patching Best Practices
Here are some of the most important SQL Server patching best practices and SQL Server cluster patching best practices you should apply when installing SQL Server patches.
- Before you apply a SQL Server Service Pack, make sure you’ve thoroughly read the list of issues and bugs addressed by the Service Pack. You can usually access this documentation on the Service Pack’s download page.
- Make sure you apply updates to development/test instances. When the instance is running without issues for a sustained period (i.e., one or two weeks), you can prepare to apply the updates to production.
- Send out an email to any users who are likely to be impacted by the update, the database instance, or any system downtime.
- To account for unexpected issues, establish a plan to facilitate a rapid rollback if necessary.
- Make sure there aren’t any SQL Agent tasks running. Consider disabling SQL Agent to avoid the risk of jobs starting or running while the Service Pack is being applied.
- Conduct a full backup of all databases (including system and user databases).
- Once the Service Pack has been applied, restart the relevant SQL instance.
- Check the SQL Server Error Log for entries pertaining to the new Service Pack to ensure no errors have been written.
- Send out an email to relevant parties informing them the Service Pack has been applied and the SQL Server is functioning as it should be.

Automate SQL Server Patching
SQL Server patching automation enables business to apply patches in a streamlined, reliable, and efficient manner. But to achieve this in a way suited to your business’s individual needs, you must choose the right tools.
SolarWinds Patch Manager is a highly sophisticated patch management tool designed to help you address software vulnerabilities. This comprehensive tool provides security patch management, such as SQL Server and MySQL security patches, by working alongside System Center Configuration Manager (SCCM) and Microsoft Windows Server Update Services (WSUS) to identify new software updates. This includes third-party application updates.
Other key features of Patch Manager include computer inventory management utilities, the ability to prevent failed Oracle Java updates, rapid deployment of security patches, remote patch management functionality, virtual patching for endpoint security, patch compliance reports, and much more. A 30-day free trial is available.
If you are looking for a database management solution with provide monitoring and analysis features, SolarWinds Database Performance Analyzer (DPA) also comes highly recommended. DPA is a database management tool that enables you to monitor, analyze, and tune SQL query performance.
SolarWinds DPA complements SolarWinds Patch Manager and includes cross-platform database support for both cloud and on-premises, real-time and historical data insights, index and query tuning advice, machine learning anomaly detection, and more. An especially useful feature is the ability to integrate DPA with the PerfStack™ and AppStack™ dashboards via the SolarWinds Orion® Platform, which allows you to centralize all your IT management and monitoring activities into a single solution. A 14-day free trial is available.
SQL Server Patching Is Critical
Although patching can be a frustrating and nerve-wracking process for network administrators and database administrators, the risks associated with unpatched software cannot be overstated. Without SQL Server patching, you expose your company to the unnecessary risk of vulnerabilities being exploited by malicious individuals. To ensure your SQL Server is safe, consider automating the SQL Server patching process and implementing the best practices listed in this guide. With the right tools at your disposal, patching doesn’t have to be complicated.
