Businesses are moving their entire infrastructure to the cloud due to its incredible virtual services, proactive support, and better scalability. However, with increased exposure to the internet and cloud, organizations’ threat surface also increases significantly. A DDoS attack is one of the most common cyber threats affecting business productivity and connectivity across the globe. Recent examples include the Estonia Cyberattack (2007), Operation Ababil (2012-2013), Mirai IoT Botnet (2016). Moreover, the cloud hosting provider Linode also became a victim of a malicious DDoS attack.
DDoS attacks are hazardous. They flood the regular traffic of the targeted network/server with a massive amount of internet traffic.
How does it work?
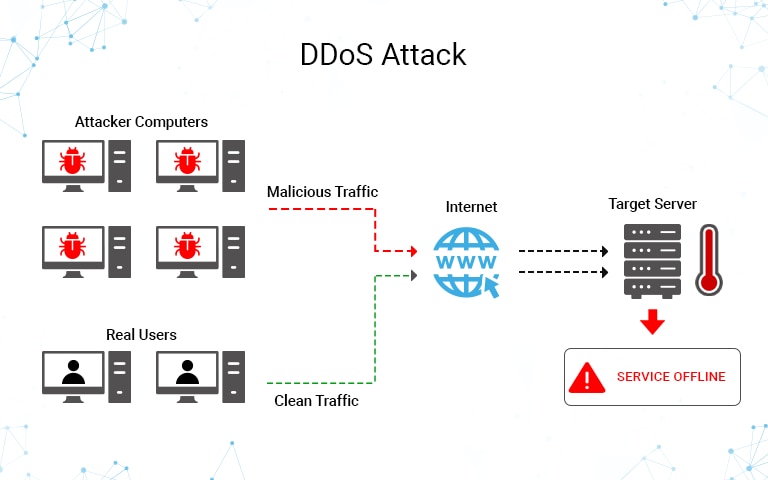
In a DDoS attack, the threat actor infects several computer systems or IoT devices with malware and converts them into a bot (zombie). The threat actor controls the infected systems remotely with and sends them updated instructions to target a particular address.
How does DDoS attack gain effectiveness?
It gains effectiveness when multiple bots start sending requests to the targeted server or network to the extent its capacity overflows, which in turn leads to a denial of service. In one of the biggest DDoS attacks ever, the BBC website was knocked out with over 600Gbps traffic.
Types of DDoS Attacks
Before knowing how to prevent a DDoS attack, it’s crucial to understand their different types. The Distributed Denial of Service (DDoS) attacks are divided into three main categories:
1. Application-Layer Attacks
The application layer is the top layer of the Open Systems Interconnection (OSI) model. The goal of application-layer attacks is to exhaust the target’s resources entirely and crash the web server. They primarily target the web pages generated on the server in response to the user’s HTTP requests. As these attacks involve fewer machines to generate higher volumes of traffic, it becomes difficult to identify whether the traffic is coming from a legitimate source or not. The most common type of application-layer attack is the HTTP flood.
2. Volumetric Attacks
Volumetric attacks are the most common type of DDoS attack. They consume the entire bandwidth of the network or attacked sites by sending false data requests. The targeted machines involve themselves in the inspection of the malicious data requests due to which they have no room left to accept the legitimate traffic. Some of the volumetric attacks include Internet Control Message Protocol (ICMP), User Datagram Protocol (UDP), and DNS Amplification. The magnitude of volumetric attacks is measured in bits per second (Bps).
3. Protocol Attacks
Protocol attacks consume the intermediate resources of the target, such as firewalls, load balancers, and connection tables of web application servers. It sends partial packets and slow pings to overload the target buffer, which ultimately crashes the system. Protocol attack includes fragmented packet attacks, Smurf DDoS, and SYN floods. These attacks can be measured in packets per second.
How to Mitigate a Multi-vector DDoS Attack?
A multi-vector DDoS attack is the most complex attack as it targets several layers of a protocol stack. Volumetric UDP amplification vectors such as CLDAP, NTP, SSDP, DNS, and Chargen are known to be the most common contributors to multi-vector attacks. The purpose of the attacker is to blend the legitimate traffic with the attacked traffic, so mitigation becomes impossible. To overcome such an attack, several strategies and layered solutions need to be in place.
- Black Hole Filtering/Routing
- Limiting Requests
- Web Application Firewall (WAF)
- Anycast Network Diffusion
Black Hole Filtering/Routing
Black hole routing method filters the network traffic through a “black hole or a null route.” As this filtration is done indiscriminately, both the legitimate and malicious traffic sources are funneled and blocked together. The process is similar to the reaction of antibiotics killing both good or bad bacteria, irrespective of their qualities.
Limiting Requests
Another way of mitigating a DDoS attack is to limit the number of server requests to a specific time window. Rate limiting not only provides security against brute-force login attempts, denial-of-service attacks but also protects the application layer from other abusive attempts.
Web Application Firewall (WAF)
The web application firewall is a defense mechanism of application layer (layer 7) which works according to a set of policies. The role of WAF policies is to protect web applications from malicious traffic by monitoring and filtering HTTP traffic. It defends against attacks like SQL injection, cross-site-scripting (XSS), cross-site forgery, and DDoS. The WAF policies can be modified anytime to activate the defense mechanisms and to take action against malicious activities.
Anycast Network Diffusion
Anycast Network Diffusion works exactly like channelizing a rushing river into separate small channels. It scatters the flood of incoming requests across a network of distributed servers, so the traffic becomes manageable, and applications can be prevented from any disruptive activity. Anycast network diffusion reliability entirely depends on the size of the attack and the efficiency of the network to withstand the onslaught.
How Log Analysis Helps in Preventing DDoS Attacks?
Preventing DDoS attacks is challenging as it comes without warning. However, with the help of individual clues, you can distinguish legitimate traffic spike from a potential DDoS attack.
Signs of DDoS Attack
A server returning 503 “Service Unavailable” error intermittently is the first sign your system could be DDoS infected. If this server error is permanent, it could lead to a server crash. However, monitoring 503 responses will be too late for you to prevent the threat as it indicates your server is already down. Monitoring 404 responses, on the other hand, can be of great help. A 404 response indicates the browser tried communicating with a given server, but the server couldn’t respond to the user’s request. With the help of baseline metrics, you can create customized alerts to get real-time notifications about the number of times the 404 has occurred.
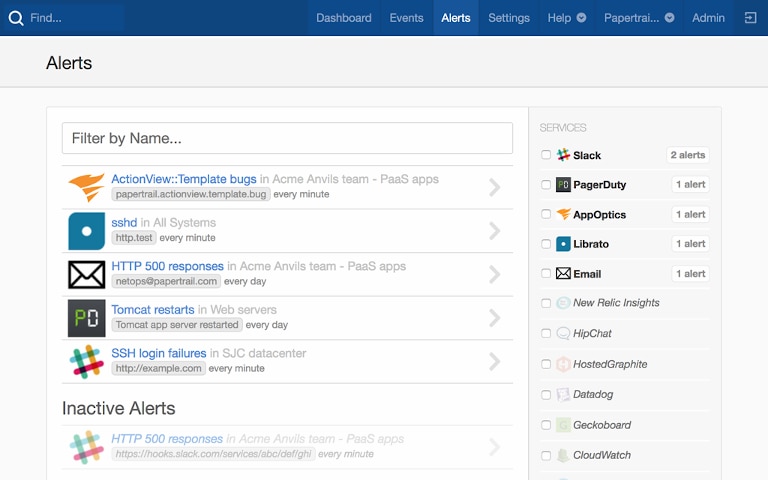
Log Monitoring and Analysis
Log monitoring is the best and the most effective way for quick identification of a DDoS threat. Logs contain raw data with loads of information capable of identifying threats in real-time. Using SolarWinds® Papertrail™, you can fetch data from different layers of the protocol stack. The tool offers a centralized logging feature using which you can parse, store, and visualize the data in powerful monitoring dashboards. The tool also provides 24/7 traffic statistics, automated reporting of ongoing attacks, intuitive web-based log viewer, powerful command-line tools, encrypted logging, REST API, search and custom alerts, and more. It also helps in identifying the number of errors returned to your users (503 and 404 responses), servers affected, and the precise date and time of unusual traffic spikes. You can also create smart event-based custom alerts by combining traffic spikes and events-based information. Doing so allows you to receive real-time notifications in the form of SMS, push notifications or emails. The tool saves you troubleshooting time by pre-informing you about the state of events.
Conclusion
Early threat detection is the most efficient way to prevent a DDoS attack. While there are sophisticated anti-DDoS solutions available in the market, not every organization is ready to implement such solutions. Further, log analysis can help you not only detect a DDoS attack, but it also gives enough context to mitigate the attack in time. We recommend cloud-based log analysis tools like Papertrail for monitoring and preventing such attacks. Learn more about the tool by visiting the Papertrail website or get a free trial here.
