As security threats and attacks become more advanced and complex, digitally modern enterprises are struggling to fight or survive these attacks and minimize the impact of these attacks on their businesses. Distributed denial of service (DDoS) attacks widely affect the internet world by interrupting the services provided to users. It’s essential to stop a DDoS attack to ensure the business continues as usual, and the experience remains seamless.
Denial of service (DoS) is commonly confused with distributed denial of service (DDoS), since both the terms have the same attack mechanism. But, distributed denial of service is an extension of DoS where a cluster of infected systems contribute to the denial of service for a larger target resource such as an enterprise network, server, or website. Let’s understand DDoS in detail.
What Is a DDoS Attack?
Distributed denial of service (DDoS) is a type of malicious attack initiated when a master source (a vulnerable system, PC, etc.) discovers and infects other weak sources within the network. The hacker then orchestrates an attack from multiple compromised systems, causing the target system or service to crash. The infected systems or devices under the control of the assailant are called bots or zombies, which collectively generate unnecessary traffic to overwhelm the target domain. DDoS is an attempt to slow down a network or shut down a server, so the service becomes inaccessible to genuine end users. The attacker or hacker exploits a vulnerability by flooding the target website or network with signals or information packets until the targeted source becomes unavailable to fulfill any genuine request. This not only forces the system to crash, but the affected availability of service leaves a negative impression on the users.
There are scenarios where multiple systems deny service or fail to complete legitimate service requests from users due to poor quality of code, unstable systems, or missing patches in systems, making it look like a “distributed denial of service” attack. While DDoS attacks are carried out by individual hackers just for fun, the motive is usually serious in most cases, targeting to damage the reputation of a competitor or a brand.
Types of DDoS Attacks
Before cracking the code of how to stop a DDoS attack, you need to know the types of DDoS attacks usually classified by open systems interconnection (OSI) model layers.
Infrastructure Layer DDoS Attacks
DDoS attacks triggered at OSI layers 3 (network layer) and 4 (transport) generally come under infrastructure layer attacks.
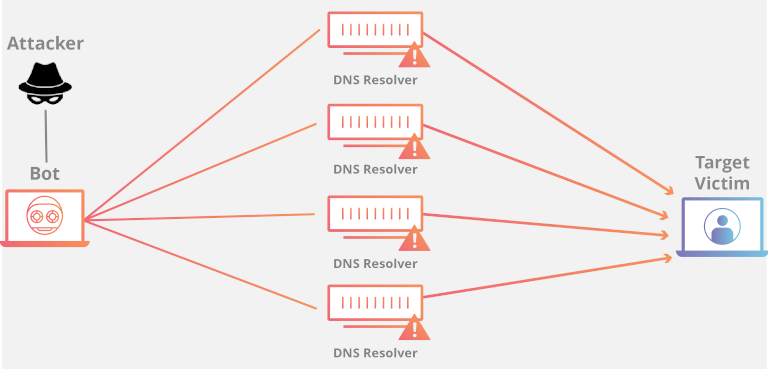
- Protocol Attacks – These types of attacks happen at the network layer or transport layer protocols where the botmaster (the attacker who controls the infected target systems) exploit flaws and vulnerabilities in the protocols (ICMP—Internet Control Message Protocol) to knock target sources offline. The hacker sends spoofed signals or packets through misconfigured devices pinging every system in the target network, overwhelming them with amplified traffic.
- Volumetric Attacks – Volumetric or network-centric attacks are the most common types. They consume entire network bandwidth or server capacity of accepting legitimate requests by using vectors for synchronized (SYN) floods or user datagram packet (UDP) floods (also known as reflection attacks). These attacks occur in large volumes and overload multiple vulnerable network resources, making the target network or application server unavailable.
Application Layer DDoS Attacks
Attacks at the 6th (presentation) and the 7th (application) layers are classified under application-layer DDoS attacks. These types of attacks target application services and databases where the assailant overloads them with a high volume of spoofed packets, such as an inundation of application calls. This type of distributed denial of service is more complicated and less common as compared to infrastructure layer attacks. Application layer attacks occur in small volumes and mainly focus on flooding costly parts of an application to make it inaccessible for real end users. Examples include SSL abuses, DNS query floods, HTTP requests flooding an expensive API, or WordPress pingback attack.
How to Stop a DDoS Attack Using the Best DDoS Protection Tool
The following are the top 3 distributed denial of service (DDoS) protection tools and software to help you mitigate the risk and secure your business from potential DDoS threats.
1. SolarWinds Security Event Manager

SolarWinds® Security Event Manager (SEM) monitors event logs from multiple different sources and detects suspicious activities to help you prevent DDoS attacks proactively.
SEM continuously monitors all your activity logs (events, traffic, user logon failures, etc.) and identifies a botnet’s (a group of infected systems under the control of botmaster or DDoS attacker) communication with command control servers. It gives you 360-degree visibility into your environment.
Security Event Manager enables you to respond to DDoS threats in real-time as it pulls out lists of known bad actors and correlates the ongoing interactions with potential command control servers. You can also define automated responses to specific activities such as malicious activity alert, automated blocking of IPs, deactivating an account, and much more.
Try out SolarWinds Security Event Manager to stop DDoS attacks targeting your company.
2. Radware DDoS Protection
Radware offers Attack Mitigation Solution (AMS) with a comprehensive set of DDoS protection services from attack prevention to mitigation across a wide range of attack vectors. Its hybrid DDoS security approach ensures end-to-end protection with integrated on-premises detection capability and cloud-based traffic services against multi-vector network and application attacks, malware propagation, server attacks, and unauthorized intrusions.
Learn more about Radware DDoS Protection and its key features here.
3. Cloudflare DDoS Protection
Cloudflare DDoS protection provides layered security with various mitigation capabilities to isolate malicious traffic, causing disruptions from good traffic, thereby making applications, websites, and APIs highly available to your users.
Its advanced automation system monitors your entire network, analyzes anomalies that can lead to DDoS attacks, and identifies the vulnerable target resources to help you take appropriate preventive actions. The software can easily interoperate and integrate with other security applications such as Bot Management, WAF, CDN, Rate Limiter, smart routing, and much more. Visit the webpage to explore more about Cloudflare’s product for DDoS protection.
