Every network has a registry containing information about its users, devices, and more. This registry or Active Directory (AD) also includes data about user groups. Each one has its own set of permission and access rights. Understanding how the directory works is critical to securing your network.
With Active Directory, you can quickly assign privileges to any existing user or group and identify empty groups that pose security issues to the entire network. If you use a tool such as SolarWinds® Access Rights Manager (ARM), you’ll be able to modify any group or entry within Active Directory quickly.
In this article, we’ll discuss the concept of Active Directory groups, the types of AD groups, and best practices for managing their information.
An Introduction to Active Directory Group Types
Active Directory is a management tool for Windows domain networks and Windows servers. It governs user permissions and restrictions for resources within the network.
If you’re a network administrator, you can use Active Directory to assign user accounts to groups, create new ones, and change their permissions with a domain controller.
There are two types of Active Directory groups you need to understand.
- Active Directory security groups: These govern access to hardware resources and user permissions. In other words, Active Directory security groups are critical to your network performance and business operations.
- Active Directory distribution groups: These exist for email distribution and work with Microsoft Exchange or Outlook. You can use distribution groups to send emails to specific subsets of Active Directory users within an organization.
From these two types of Active Directory groups, you’ll spend more time dealing with the first one. Active Directory security groups can help you exercise access control over critical assets within your network.
Security groups can help prevent unauthorized users from gaining access to sensitive information. However, you’ll need to follow Active Directory group management best practices.
Active Directory security groups can vary in user bases. In a nutshell, you have local, domain local, global, and universal access entities. Local groups are only available on a single computer, whereas domain local groups can exist anywhere within a network.
Global groups can include collections of domain objects, including users, hardware, and other subgroups. This flexibility makes them perfect for assigning permissions to entire departments.
Finally, universal groups are ideal for networks spanning multiple domains. They can govern permissions you can replicate on other servers.
An Overview of Active Directory Group Management Best Practices (3 Key Tips)
Managing an Active Directory security group can be a challenge. In general terms, you want to ensure no user or group has access to more permissions than they need.
However, this principle applies to almost any network. So, let’s be a bit more specific, starting with audits.
1. Monitor Active Directory Logs
Depending on which Active Directory management tool you use, you should have access to extensive logs that can tell you about standout events.
For example, you should be able to view failed login attempts. You can also check to see if anyone has made changes to group permissions, added or removed users, and more.
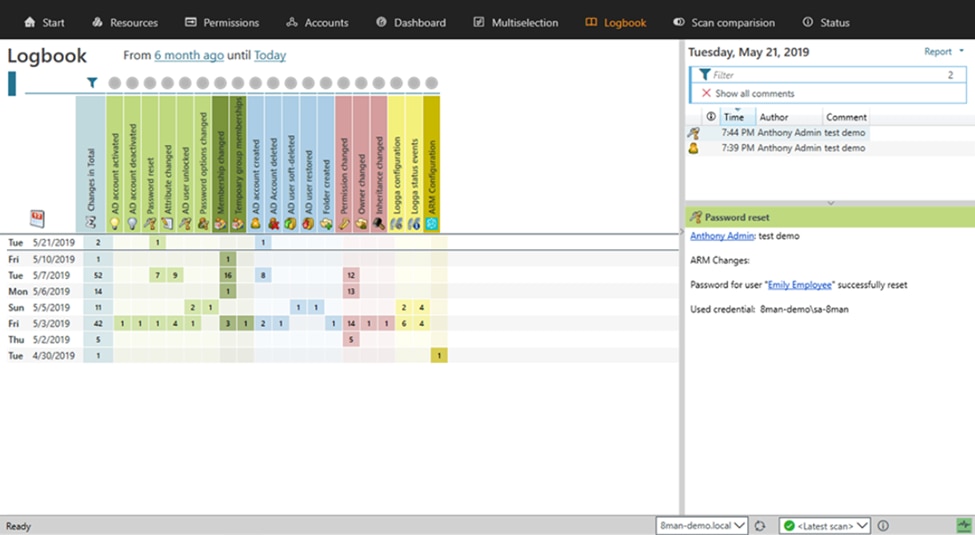
Ideally, you should audit your Active Directory often to avoid missing critical security events. If you see spikes in suspicious activity, it’s time to review your existing groups.
In this scenario, you’ll be looking for which users are abusing their current permissions. Then, you can revoke them to maintain network security.
2. Identify and Remove Empty Security Groups
In theory, there shouldn’t be any Active Directory groups without any users. It defeats the purpose of having groups in the first place.
However, in practice, it’s standard for your Active Directory to end up with multiple empty groups as the network grows.
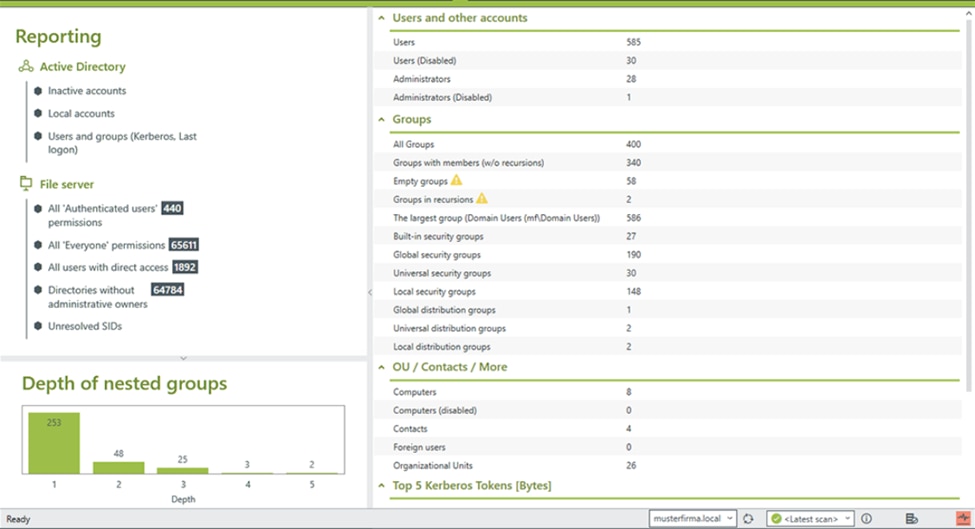
There are two key issues with having empty Active Directory security groups. First, they clutter the directory, making management more difficult, even if you have access to user-friendly Active Directory tools.
The second and most significant issue is empty groups pose security risks for your network. Think about every empty Active Directory security group as an additional attack vector for malicious actors. Having empty groups within the network makes it easier for hackers to find a way in and gain access to secure data and hardware.
Depending on which Active Directory group management software you use, you should have access to different tools. They will enable you to identify empty Active Directory groups and either delete or consolidate them. If any groups share similar permissions, then combining them can be the intelligent thing to do.
3. Configure Your Default Groups
When you create a directory within Active Directory, the software generates several default security groups. They tend to have high permission levels, which might be excessive for most users within your organization.

As a rule of thumb, try to identify if there’s an Active Directory group with too many permissions. If there is, you need to modify the privileges or restrict who has access to the group.
For example, you should never provide users with access to the domain admins group unless they’re active domain administrators.
When setting up an Active Directory domain, you should first map out the groups your organization needs. You can also allocate which permissions each of them requires. Then you can assign users to those groups and ensure no one has access to more privileges than they need.
Conclusion
Active Directory is a powerful service for managing which resources users can access within Windows servers and networks. However, it is only as good as its administrators and the groups that they create. If you want to manage Active Directory more efficiently, we recommend looking into tools such as SolarWinds Access Rights Manager.
Regardless of which Active Directory management tool you use, you’ll also want to follow best practices, including:
- Monitoring Active Directory logs
- Identifying and removing empty security groups
- Configuring your default groups
Use our recommended SolarWinds ARM software to efficiently manage your AD and control the security status of your user accounts. With a free trial, you can use all the features of this tool right after installation. Download now.
