One of the major tasks of IT administrators is to manage their assets across enterprise networks efficiently. They need to keep a close check on user authorizations across the network and manage permissions. As organizations grow, however, they expand their network, which also increases their threat surface. Misconfigurations or failures in implementing authentication, authorization, and accounting (AAA) policies often lead to data breaches and compliance lapses. Keeping track of orphaned accounts and countering privilege escalation attacks also becomes challenging. In this complex and ever-evolving threat landscape, efficient management of Active Directory (AD) is of primary importance.
What Is Active Directory?
Active Directory helps IT teams monitor various network objects, grant and revoke different user permissions, and implement policies for smooth operations within a network. For example, an admin can create a group of users and allocate them specific access permissions to directories on the server. As the network grows, however, it can become difficult for admins to track users, login details, resource allocation details, and permissions. Active Directory is one of the most important IT infrastructure tools, and it helps admins manage user provisioning processes, security, and audits and provides access to each user’s account from a single location. With the help of Active Directory, users can be organized logically into groups and subgroups to provide access control.
Active Directory is a Microsoft product and runs on Windows Server operating systems. It includes several services to manage permissions and provides access to resources in a network.
In Active Directory, data is stored as objects. An object can be understood as a single element, such as a user, group, application, or device. Objects can either be resources or security principals like users or groups. Every object has a name and attributes. For example, a user’s name might be a combination of a name string and information associated with the user.
The Active Directory structure is comprised of three main components: domains, trees, and forests. Several objects, like users or devices that use the same AD database, can be grouped into a single domain. Domains have a domain name system (DNS) structure. Multiple domains can be combined to form a group known as a tree. The tree structure uses a contiguous namespace to arrange domains in a logical hierarchy. Different domains in a tree share a secure connection and trust each other in a hierarchy. This means the first domain can implicitly trust the third domain in a hierarchy. A collection of multiple trees is called a forest. Admins can allocate specific access rights and communication privileges at all levels. Moreover, a forest also includes directory schemas, shared catalogs, domain configurations, and application information. The global catalog servers provide a list of all the objects in a forest, and the schema defines the class and attributes of an object in a forest. Organizational units (OUs) organize groups, users, and devices. Every domain can contain its own OU.
Active Directory provides several services like Domain Services, Lightweight Directory Services, Certificate Services, Federation Services, and Rights Management Services. These services fall under Active Directory Domain Services (AD DS). AD DS comes with Windows Server and is designed to manage client systems. AD DS can be considered the main service of Active Directory; it stores directory information and takes care of the interaction between the user and the domain. When a user tries to connect to a device, server, or resource over a network, AD DS checks the login credentials and access permissions given to the user. Other products like SharePoint Server and Exchange Server also depend on AD DS for resource access.
Active Directory Certificate Services (AD CS) creates, shares, and manages certificates. These certificates enable users to exchange information over the internet securely.
Active Directory Lightweight Directory Services (AD LDS) has the same function as AD DS. AD LDS can store directory data using Lightweight Directory Access Protocol (LDAP) and run numerous instances on a single server. The LDAP application protocol stores data related to objects in directory services, like usernames and passwords, and shares them across the network.
Active Directory Federation Services (AD FS) uses the concept of single sign-on (SSO) to validate users, and it allows them to access multiple applications on different networks in a single session. With SSO, users need to sign in only once for each service.
Active Directory Rights Management Services (AD RMS) protects confidential and discrete information from unauthorized access by encrypting the content on a server.
Active Directory comes with Microsoft Server operating systems and offers a diverse set of features and services. Active Directory helps IT professionals allocate access rights to new hires (account provisioning) and revoke access rights for employees who are leaving the company (account de-provisioning). While Active Directory Domain Services plays a vital role in organizations, it doesn’t natively provide security against cybercrimes. If there’s suspicious activity, IT teams need to go through logs manually and spend time pinpointing areas in need of rectification. This is because the integrated tools that come with Active Directory may not be very effective or helpful at the enterprise level.
Active Directory management tools help overcome these issues. Fortunately, it’s easy to enhance the capabilities of the existing Active Directory suite with third-party software or tools. From automated alert systems to reporting capabilities, there are plenty of products available to fit your needs.
Companies need to understand their requirements and choose the best Active Directory management tools for their needs. Moreover, the third-party software they choose should work well with the existing digital environment and resolve issues related to cybersecurity and networking.
Active Directory management (AD management) ensures Active Directory is working as required. AD management is the process of managing and monitoring the operations of the Active Directory services found in Windows Server operating systems. AD management is also a part of the network or server monitoring and management processes.
Active Directory monitoring can help automate Active Directory user provisioning processes, comply with regulations and audits, provide security, and grant access to users’ accounts from a central location. Network administrators using AD and Windows Server’s native administration and management features can perform this service manually. This process can also be performed using customized software designed to automate Active Directory monitoring.
Benefits of Implementing an Active Directory Environment
A Better Representation of the Network
The Active Directory structure provides a clear picture of the network. Active Directory allows admins to centrally manage users and authorizations, regardless of the size of the network. A centralized approach to management is one of the most important reasons to implement Active Directory.
Single Sign-On Capability
Imagine a situation where a user has to memorize several passwords and usernames for various servers. This situation can become even more complicated, especially when the number of users increases. To simplify this, a domain controller can be added to the environment. The single sign-on (SSO) capability of the domain controller allows users to enter their usernames and passwords on one server and access other servers without having to enter these details again.
Efficient Management of Trust Relationships
Active Directory allows the use of trust relationships among various domains. This means that a two-way trust relationship can exist between two entities. For example, if there is a two-way trust relationship between two websites, the users can use the resources on both sites with a single password and username.
Centralized Policy-Based Management
Centralized policy-based management is another benefit of Active Directory. This feature helps manage and improve the security settings of workstations from a single point. This means admins can monitor, control, and manage the security settings of all the network resources from a single point.
Improved Scalability With Organizational Units
Active Directory uses the concept of organizational units (OUs) to improve scalability in large organizations. An OU can be defined as a collection of users and computers. When companies have large domains, they can be organized into OUs. For example, a company has a huge HR department and there is an admin managing the entire domain. The company can create an OU named HR, and all the user accounts and computers related to HR can be moved to it. The admin who is responsible for this OU can be given certain administrative rights limited to this OU.
Multi-Master Replication and Sites
The concept of multi-master replication and sites is another amazing benefit of an Active Directory environment. Every domain controller contains a copy of Active Directory in an Active Directory multi-master replication environment. Whenever a change is made to Active Directory, the closest domain controller will update accordingly. Other domain controllers in the environment will also update themselves. This concept also applies to sites. Each site has its own domain controller, so when a user within a site updates the Active Directory, the changes are reflected in the domain controller within the site. The domain controller on the other side of the site will also update the changes at regular intervals.
How Does Active Directory Work?
When you begin installing a Windows computer, all the systems are workgroups or standalone computers. There’s no domain present at this stage. Such an environment includes several systems, workstations, or servers with separate passwords and usernames.
With the help of Active Directory, you can organize all the information related to users, systems, and devices in a single place. The information related to the Active Directory, users, groups, and passwords is stored in an AD database known as the NTDS.DIT file (NT Directory Services).
Initially, all the systems are separate devices. To reap the benefits of Active Directory, the Active Directory Domain Services must be installed on a server. This server contains the NTDS.DIT database file. Information about users, computer accounts, user groups, and passwords will be stored in this database file. After the creation of the file, admins can create a domain controller. A domain can have multiple domain controllers.
Active Directory uses a security mechanism known as Kerberos. Once the user enters his or her login details, Kerberos grants a Ticket Granting Ticket (TGT) to the user through a ticket-granting system. The user then presents this ticket to other workstations and servers throughout the same domain (or even on other domains where a trust relationship exists). The servers identify the ticket and understand it’s been issued by a trusted domain controller. After authorization, the users get the permissions necessary to complete their intended tasks.
Active Directory maintains consistency among several domain controllers. It’s possible to have multiple domain controllers in an environment. Large organizations normally have multiple domain controllers, so admins must ensure all the domain controllers contain the same information. To maintain consistency, Active Directory implements synchronization mechanisms to ensure all domain controllers have consistent data.
top 8 Best Active Directory Management Tools
- SolarWinds Access Rights Manager (ARM)
- Dameware Remote Everywhere
- Dameware Remote Support
- SolarWinds Server & Application Monitor (SAM)
- Anturis
- XIA Automation
- ManageEngine ADAudit Plus
- Z-Hire and Z-Term
1. SolarWinds Access Rights Manager (ARM)
SolarWinds® Access Rights Manager™ (ARM) allows admins to manage and audit Active Directory and keep track of user access across the IT infrastructure. This tool delivers customized Active Directory (AD) and Azure AD reports and shows which users have access to resources and when they access them. The tool also allows admins to set up automated report scheduling and deliver these reports directly to auditors to speed up assessment.
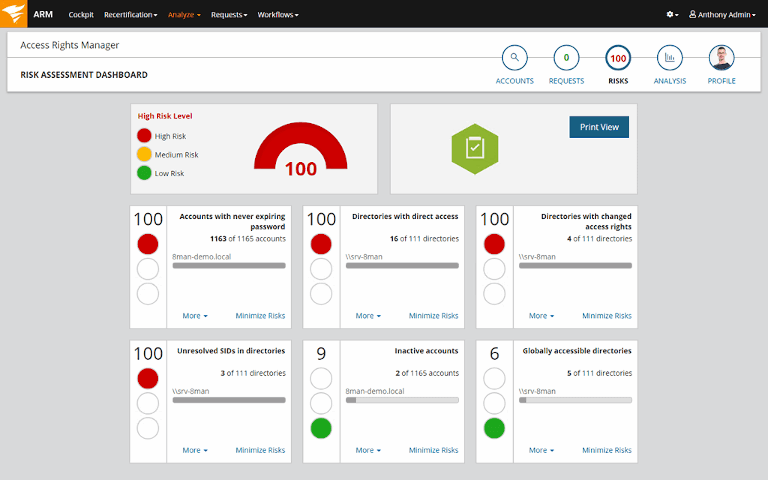
Using this tool, user permissions can be granted and revoked (also known as user provisioning and de-provisioning) in a matter of seconds. ARM also includes built-in features for monitoring cybersecurity threats. Other Active Directory management tools can complicate the process, but ARM is a preferred tool to reduce the workload of the IT team and help them securely delegate AD permission to data owners. SolarWinds ARM can help spot user accounts with insecure configurations and protect against theft and misuse of authorization and access.
2. Dameware Remote Everywhere
SolarWinds Dameware® Remote Everywhere (DRE) is a cloud-based remote support solution accessible from anywhere with a fast internet connection. This simple and lightweight tool is best for IT admins who want to provide remote support on issues related to AD. The robust reporting capability of this tool records session details, information about the performance of technicians, and end-user survey summaries. This tool’s main advantage is it shortens the time required to resolve issues and avoids long connections or software response times. It can also provide remote support to sleeping or powered-off systems. The tool is easy to use and install, and companies can register for a 14-day, risk-free trial version of DRE.
3. Dameware Remote Support
SolarWinds Dameware Remote Support is one of the top tools supporting remote IT tasks across various platforms like Windows, Linux, and Mac operating systems. This tool allows admins to manage user accounts, manage permissions, and control Dameware environments from a single, central location. Information related to AD properties, system configuration, and software can be exported in different formats. With this tool, admins can unlock accounts, reset passwords, and change group policies from a single dashboard.
4. SolarWinds Server & Application Monitor (SAM)
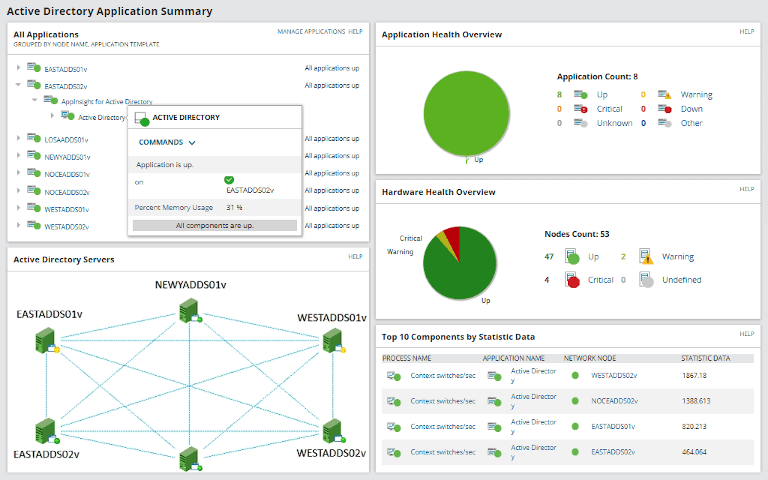
SolarWinds Server & Application Monitor (SAM) is a comprehensive server and application monitoring tool that helps admins monitor Linux and Windows applications and environments across private, public, and hybrid cloud environments. This tool helps diagnose replication errors and gain deeper insights into the workings of various domain controller replications.
The SAM Active Directory monitoring solution helps you drill into each site and collect information like site link names, subnets, and IP ranges to quickly understand Active Directory issues and troubleshoot them remotely. SAM’s Active Directory auditing tool allows admins to keep track of login and password information. Admins can perform several IT tasks from a single, customizable web interface. Thus, SAM can greatly enhance Active Directory management.
5. Anturis
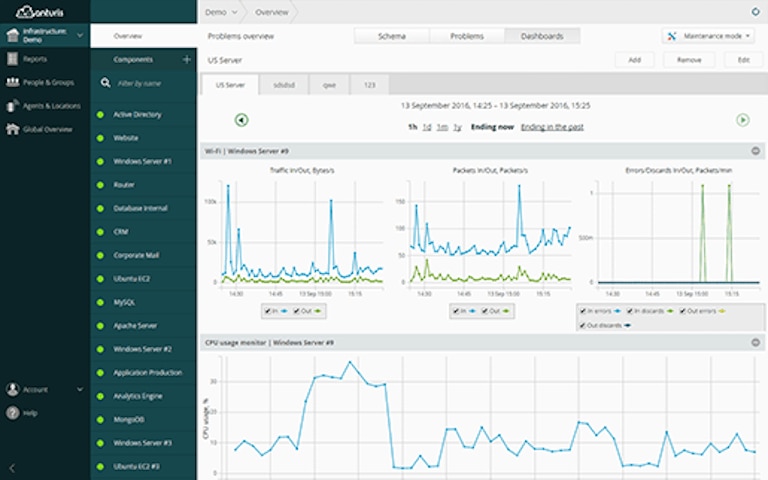
Anturis is a comprehensive tool and a complete cloud-based monitoring application solution. This tool offers several services to help take care of potential problems before they impact Active Directory. The tool provides information related to server sessions and shows the number of users that may be accessing the directory servers. This diagnostic service also takes care of performance trends. It sends timely alerts through email or SMS notifications whenever there is an error. Anturis also creates performance baselines for your directory servers and replicates the structure to tackle potential bottlenecks.
6. XIA Automation
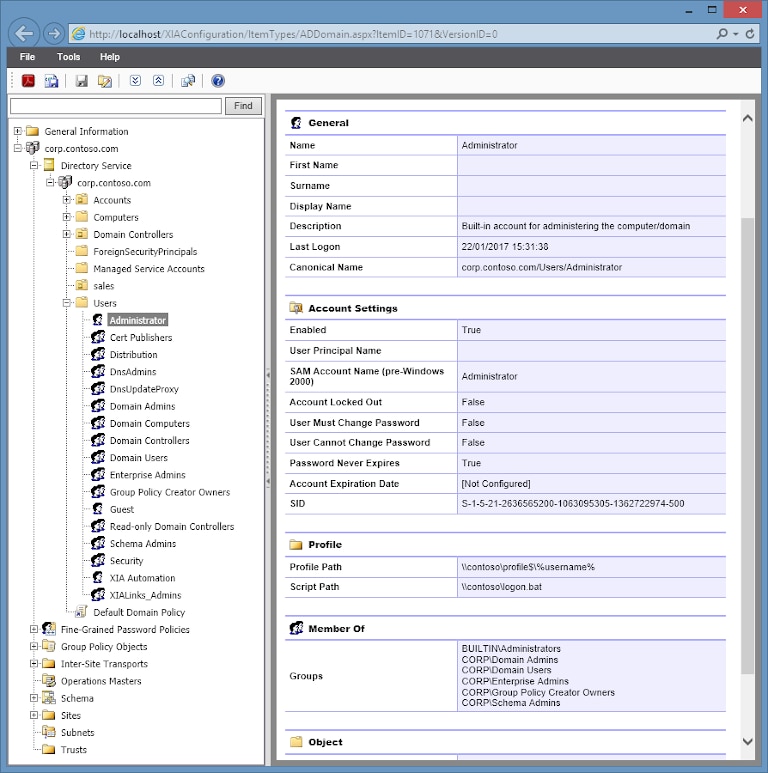
XIA Automation is a great network task automation tool. It helps admins automate groups, AD user accounts, and organizational units. This tool offers many options to save IT teams’ time and effort. XIA Automation allows bulk provisioning of user accounts from comma-separated values (CSV) files to Office 365, AD, Google, and Exchange. Users can also reset passwords from their mobile devices. The tool creates several Microsoft Exchange accounts and mailboxes in a few minutes.
The platform gives users the liberty to create custom plugins to match specific AD management requirements. It’s also possible to access XIA Automation from your mobile devices and perform tasks when you’re traveling. Its user-friendly and intuitive web interface allows users to perform tasks on desktops or mobile devices. XIA Automation is packed with features and is used by several schools and other educational institutions to streamline Active Directory management.
7. ManageEngine ADAudit Plus
Companies can conduct real-time auditing for Active Directory with ManageEngine’s ADAudit Plus tool. This tool provides advanced auditing capabilities along with essentials for AD management. Features like timely email alerts, predefined reports, and advanced tracking capabilities allow admins to keep track of changes in the network around the clock. This tool offers the ability to tap insider threats and can check on the activity of users in Windows Server environments. Companies can download a free edition of the tool capable of auditing 25 workstations.
8. Z-Hire and Z-Term
Introduced by Zohno, Z-Hire and Z-Term are two tools designed to speed up the processes of account creation and account termination, respectively. With Z-Hire, administrators can create user accounts for Exchange mailboxes. By simply clicking a button, admins can simultaneously create Lync accounts and Exchange mailboxes as well as Active Directory user and Salesforce user accounts. Z-hire can save time on account deployment. Z-Term works in the opposite way: it streamlines the process of employee termination. With Z-Term, all the important and necessary tasks required when a team member leaves a company can be performed automatically. The tool ensures former employees can no longer access the company’s resources after termination. The platform supports features like group deletion and resetting passwords, and it updates the group membership information.
Conclusion
Although Active Directory is a popular service, it’s not very efficient in terms of management and convenience. If we use third-party tools along with the AD administrative tool kit, we can extract a lot more from Active Directory and manage user access as well as account provisioning and de-provisioning tasks more effectively.
The most apt Active Directory management tool for your organization will depend on your needs, the size of your teams, and the structure of your network. Solutions like SolarWinds Access Rights Manager can help you manage the AD environment and meet your security requirements. SolarWinds Server & Application Monitor is also a comprehensive monitoring solution supporting Active Directory monitoring. You can evaluate these solutions with their free trials and implement them to simplify monitoring your AD servers.
