In IT operations, ensuring secure and reliable communications over different networks is a crucial requirement. IT administrators have to rely on different protocols, networking best practices, and network monitoring tools to ensure the flow of data in a network meets various standards for security and Quality of Service (QoS). One of these common practices is known as packet sniffing, which helps IT administrators keep track of packets (small formatted units of data) and ensure they’re transferred smoothly. While the packet sniffing technique is often associated with cyberattacks, it’s commonly used by internet service providers, government agencies, advertisers, and even large organizations for network monitoring. In this article, we’ll discuss packet sniffing in detail and also explore commonly used tools by IT practitioners.
What Are Packets, and Why Do We Need Packet Sniffers?
All networks consist of several components, such as workstations, servers, networking hardware, and more. In the networking terminology, all these components are called nodes. A healthy network connection ensures the data between these nodes is transferred reliably and at an acceptable speed according to the bandwidth and throughput of the network. While most of the traditional networks maintain physical or wired connections, modern networks are a mix of physical and wireless connections. However, the concepts of data transfer in all such networks remain the same.
In networking, the data is transferred in the form of packets, or small chunks of data. These packets vary in their format, depending on the network protocol (TCP/IP, UDP, etc.). In addition to the actual information or data, all packets contain control information designed to help in the delivery of packets from source to destination. The control information is required as packets intended to be transferred to a specific node often pass through several nodes in a network and can end up at the wrong node. The control information includes IP addresses of the sender and the receiver, packet sequencing information (e.g., packet number), and more to ensure packets reach the right destination. However, the transfer of packets in a network can get disrupted due to several issues and network errors.
In protocols like TCP/IP, there’s no inherent mechanism to recover the packets lost in transmission. However, network architects use the protocol in only fault-tolerant networks, where losses below certain thresholds are acceptable and don’t affect the communication. However, in protocols like UDP, the sender continues to resend the packet until it receives the acknowledgment of receipt from the receiver. While it adds reliability to the transmission, it also increases resource consumption. If left unchecked, it can lead to significant delays in overall transmission rates. This is where packet sniffers offer a solution.
With a packet sniffer, sometimes also called packet analyzer, network administrators can monitor their network traffic and gain valuable insights about their infrastructure and its performance. It allows them to measure the traffic flow in a network and also identify which applications are using the maximum bandwidth.
How Do Packet Sniffers Work?
As discussed above, when a sender transmits data packets, the packets pass through several nodes in a network. Each network adapter and the connected device examines a packet’s control information to see what node the packet is headed toward. Under normal circumstances, if a node finds the packet is addressed to some other node, it drops or ignores the packet. However, in packet sniffing, certain nodes are programmed to not follow this standard practice and collect all or a defined sample of packets, irrespective of their destination address. The packet sniffers use these packets for the analysis of a network.
Depending on who’s using the packet sniffers, it can have both positive and negative use cases. Threat actors can extract critical information from unencrypted messages. Many times users logging into websites over unencrypted transmission expose their credentials (user ids, passwords, etc.) in plain text, which can be easily intercepted by packet sniffers. However, packet sniffing also offers many benefits we’ll discuss later in this article.
Types of Packet Sniffers
There are two major types of packet sniffers:
Hardware Packet Sniffers
As the name suggests, it’s a hardware component plugged into a network for packet sniffing or network analysis purposes. Hardware packet sniffers are commonly used when network administrators have to analyze or monitor a particular segment of a large network. With a physical connection, these packet sniffers allow administrators to ensure all packets are captured without any loss due to routing, filtering, or any other network issue. A hardware packet sniffer can have the facility to store the packets, or they can be programmed to forward all captured packers to a centralized location for further analysis.
Software Packet Sniffers
Software Packet Sniffers are the more common type of packet sniffers used by many organizations. Every computer or node connects to the network using a Network Interface Card (NIC), which is generally configured to ignore the packets not addressed to it. However, a Software Packet Sniffer changes this behavior, so one can receive every bit of network traffic for analysis. The NIC configuration is known as promiscuous mode. The amount of information collected depends on whether the packet sniffer is set on filtered or unfiltered mode.
Depending on the size and complexity of a network, multiple packet sniffers might be required to monitor and analyze a network effectively. This is because a network adapter can only collect traffic from one side of a switch or a router. Similarly, in wireless networks, most network adapters can connect to only a single channel at a given time. To capture packets from other channels, one has to install multiple packet sniffers.
Top 5 Benefits of Packet Sniffing
- Detecting the Root Cause of a Network Issue
- Troubleshooting Network Issues
- Traffic Analysis
- Bandwidth Management
- Network Security and Compliance
1. Detecting the Root Cause of a Network Issue
Today, in most enterprise networks, there are several user groups and applications, along with a complex mix of legacy and next-gen networking equipment. Ensuring all applications and servers perform without any performance bottlenecks is a huge undertaking. When an application or a service experiences an issue, it can be a difficult task to identify which network or application component is responsible for the slowdown. This is why network administrators monitor their network continuously for routine maintenance and optimization. With packet sniffers, they can collect information from all points of their network to quickly identify the components responsible for latency, jitters, or packet loss.
2. Troubleshooting Network Issues
Whenever IT teams receive tickets related to network connectivity, they can perform PCAP analysis to measure the response times or latency in a network. It helps in determining the amount of time a packet takes to travel from a sender to a receiver. With this analysis, teams can identify congested links, detect the applications generating an unusual amount of traffic, and take remedial actions to resolve the issue. Using modern Wi-Fi packet sniffers, teams can get performance metrics for different access points and wireless controllers. Many advanced network monitoring tools offer additional features for fault, performance, and network availability monitoring. It’s also possible to correlate network data across the stack and perform hop-by-hop network path analysis to troubleshoot network issues and minimize network downtime.
3. Traffic Analysis
IT teams can also collect the packet data for predictive analysis. They can visualize this data to detect the peaks and troughs in network demand over longer periods. Using advanced IP sniffers and packet analyzers, they can categorize the data based on destination server IP addresses, ports involved in communication, the volume of traffic, and more. With all this analysis, it’s possible to distinguish critical traffic (required for VOIP, ERP suites, CRMs, etc.) from non-business traffic (social media, unauthorized messengers, etc.). Also, IT administrators can filter and flag suspicious content.
4. Bandwidth Management
Slow or intermittent networks can significantly impact business productivity and lead to huge losses. Businesses rely on advanced network monitoring tools to avoid such issues. However, most of these tools also rely on packet sniffing to analyze the traffic in a network. Packet sniffers help in preventing the misuse of the network by both internal and external users. As discussed above, with traffic analysis, IT teams can easily identify the traffic flow and WAN bandwidth utilization, any irregular increase in network usage, and more. Equipped with this data, they can prioritize bandwidth allocation for mission-critical applications, and even restrict certain applications.
5. Network Security and Compliance
It’s not rare for threat actors to infiltrate an enterprise network and compromise sensitive data. However, their activities can also remain hidden for a long period, and many times they use advanced malware to make malicious use of enterprise resources. Regular traffic analysis allows the detection of any suspicious increase in outbound traffic flow. Packet sniffers help in detecting a surge in traffic, attempts at network intrusion, and enable deeper evaluation and mitigation of security threats. They help in checking the status of WAN and endpoint security systems. Packet sniffers also help in regulatory compliance documentation by logging all of the perimeter and endpoint traffic. Moreover, with packet sniffers, security teams can verify the effectiveness of their security setup consisting of several firewalls, web filters, WAF, IPS/IDS systems, and more.
Best Practices for Packet Sniffing
There are many network monitoring tools offering packet sniffing features. You can also find several open-source applications for packet sniffing. It’s possible to select one of these packet sniffers, set the NIC to promiscuous mode, and start capturing packets from a network. However, before jumping into action, you must understand how to make the most of packet sniffing techniques, without compromising your network. Here are some of the best practices for getting started:
Understand Your Monitoring Requirements
While various network monitoring tasks are automated today, IT practitioners still rely on heuristics and manual analysis to detect issues and resolve network problems. A strong understanding of networking concepts is essential for network monitoring. When using a packet sniffer, experienced teams often opt for the filtered mode to capture only the specific information from the packets. Collecting all packet data and not knowing what information is crucial for analysis can lead to information overload.
Bolster Security
All packets contain control information (e.g., source and destination IPs) and the actual data or payload during the data transmission. It’s important to ensure the payload is encrypted during all data transfers, as packet sniffers can also capture this data, and any sensitive information can inadvertently get exposed if encryption isn’t in place. As an added layer of security, IT teams can configure their packet sniffers to copy only the header data as it’s sufficient for most of the network monitoring and analytics.
Implement Packet Sampling
While restricting the packet sniffing to packet headers reduces workload and storage requirements, it can still lead to a large volume of data and fill up disk space quickly. Packet sampling can help in resolving this challenge. Instead of collecting data from every packet, IT teams can copy packet data at set frequencies (e.g., every 10th or 12th packet). While this sampling may not provide the most accurate picture, it provides satisfactory results over longer periods of monitoring.
Top 8 Packet Sniffers
- SolarWinds Network Performance Monitor
- ManageEngine NetFlow Analyzer
- PRTG Network Monitor
- Wireshark
- Tcpdump
- OmniPeek Network Protocol Analyzer
- NetworkMiner
- Colasoft Caspa
1. SolarWinds Network Performance Monitor
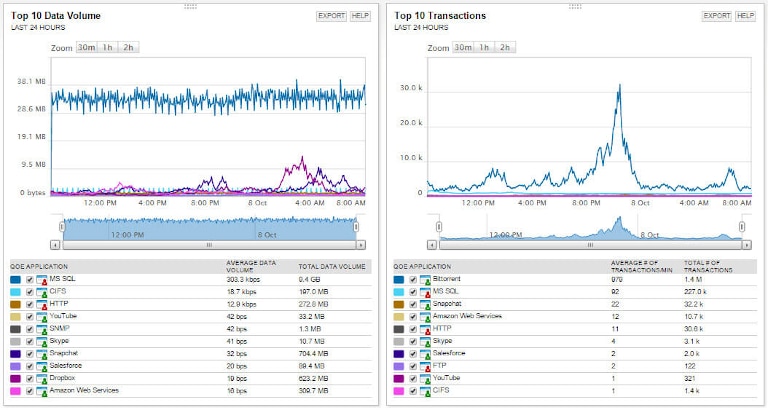
SolarWinds® Network Performance Monitor is an advanced network monitoring tool allowing you to monitor availability and security parameters with intelligent mapping, pre-configured dashboards, and advanced alerting features. With its network packet sniffer, you can get to the root cause of network issues and troubleshoot errors quickly. The tool identifies more than 1,200 applications, which makes it easier to analyze traffic and identify what’s leading to a poor end-user experience. It allows you to calculate response times for different applications, along with their data volume, and other performance indicators to categorize the traffic into different types and risk levels. You can use the Quality of Experience dashboard to get a holistic view of several metrics related to the network and application performance.
Network Performance Monitor also provides a simple visualization of traffic levels allowing you to identify any unusual spikes, which could be an indication of a security breach. While packet sniffing is one of the important features, Network Performance Monitor also offers several other advanced features, used by teams running network operations centers. With this tool, you can automate device discovery, perform latency tests, conduct network path analysis, implement SNMP monitoring, create Wi-Fi heat maps, get visual traceroute from NetPath analysis, and more. The tool can automatically poll a network for updates every five minutes. Its automated network alert feature helps in identifying critical issues immediately.
2. ManageEngine NetFlow Analyzer
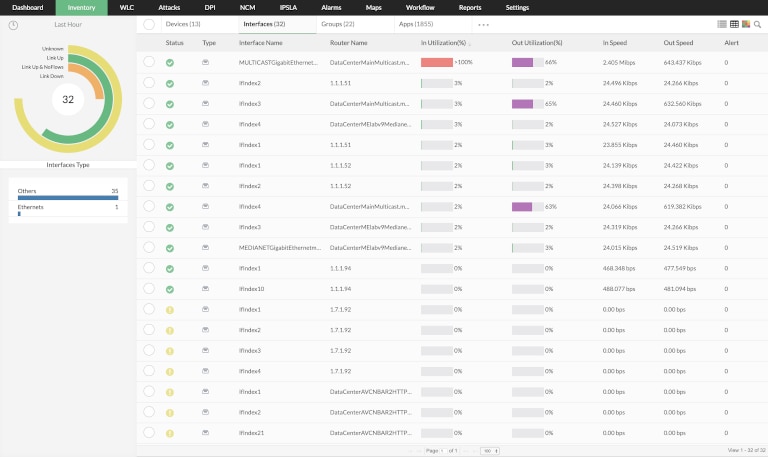
ManageEngine NetFlow Analyzer is a comprehensive traffic analysis software capable of being installed on both Windows and Linux systems. It offers packet sniffing and passively monitors network sessions to extract details like IP addresses, host names, open ports, etc., without interfering with the data transmission. It offers a Deep Packet Inspection (DPI) add-on, which allows capturing packets from the network flows and analyzing the PCAP files. The add-on enables packet-level analysis to identify any application issues. It also includes granular visibility into bandwidth consumption across different applications in an enterprise network. IT teams can also monitor response times for troubleshooting purposes. Learn more about NetFlow Analyzer’s packet-sniffing capabilities here.
3. PRTG Network Monitor
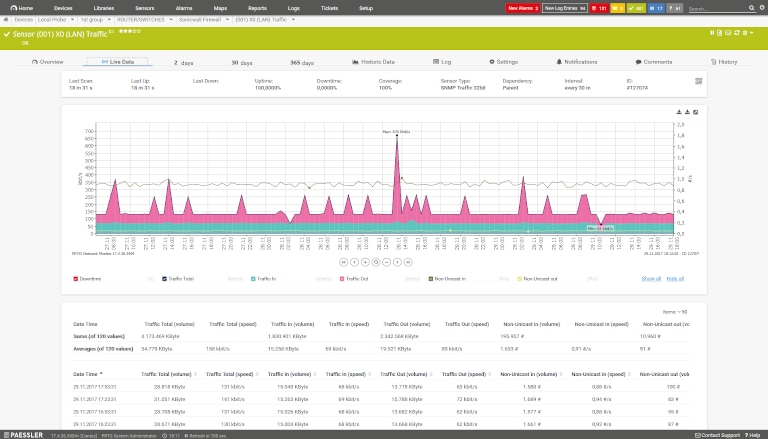
PRTG Network Monitor is another popular network monitoring tool, designed to simplify packet capturing and analysis. It offers more than 200 sensors for monitoring different parts of a network. IT teams can make use of four core sensors viz Packet Sniffing, SFlow, NetFlow, and JFlow for sniffing IP packets. The sensors are designed to meet varied monitoring requirements; for instance, the packet sniffing sensor only captures packet headers and can be useful in monitoring traffic from emails, web servers, file transfers, and more. The SFlow sensor offers packet sampling, while NetFlow and JFlow sensors are designed for Cisco and Juniper devices, respectively. While the tool is easy to implement, you may have to install multiple sensors based on the size of your network, which also affects its pricing. You can learn more about the tool and its capabilities here.
4. Wireshark

Wireshark is a free and open-source packet analyzer tool, designed to support multiple platforms, including Windows, Linux, Solaris, FreeBSD, NetBSD, macOS, and more. In addition to connections using Ethernet, it can analyze live packet data from different types of networks, including Wireless LAN, USB, Bluetooth, and more. You can also send packet data from other packet sniffing programs to Wireshark for analysis. Deep inspection and decryption support for multiple protocols, powerful display filters, and offline analysis make Wireshark a highly useful tool for packet analysis and network monitoring. Being an open-source tool, it may pose certain challenges in configuration and upgrades; however, the tool is highly popular among network administrators, security engineers, QA teams, and developers.
5. Tcpdump
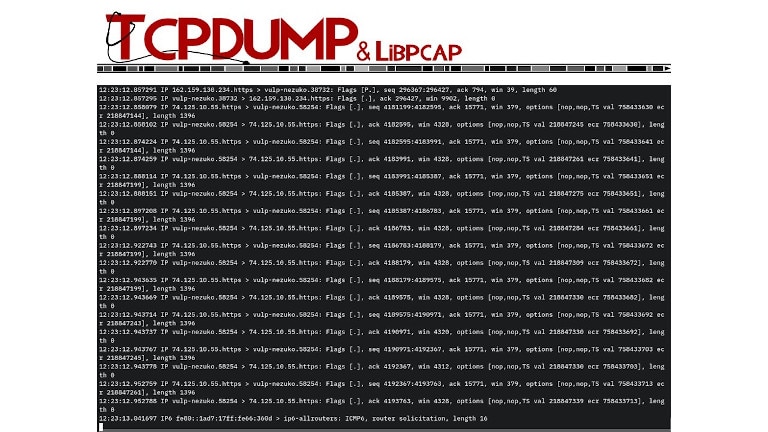
Most system administrators are familiar with tcpdump, which is one of the oldest utilities for packet capturing. The command-line utility works on Unix or Unix-like (Linux, Mac OS) operating systems, and can be installed for free. For Windows, you can install Windump, which performs similar to tcpdump. The packet capturing feature of tcpdump is available under the libpcab library. When the program is run, it starts capturing packets and displaying their contents. The program may keep running forever until you specify a limit in advance or manually terminate the session with a command. However, analyzing this data can be a complex task as one has to learn several commands to filter and segment the data. This is why most teams forward the packet data to tools like Wireshark to analyze the data captured by tcpdump.
6. OmniPeek Network Protocol Analyzer

Omnipeek Network Protocol Analyzer is a powerful monitoring tool offering advanced visualization, and quick resolution of network and application issues. It offers both flow-based and packet analysis features for real-time network analysis. The tool also supports Wi-Fi packet analysis; however, you’ll have to install various plugins to capture packets as the core software doesn’t offer packet sniffing. It can provide a detailed view of traffic by their protocol and throughput, using live charts and graphs. It also helps admins measure the transfer speeds and can raise threshold-based alerts. You can learn more about the tool and its advantages here.
7. NetworkMiner
NetworkMiner is another open-source tool used for packet sniffing and analysis. It’s a Windows-based tool but can also help in packet capturing on Linux, Mac OS X, and FreeBSD. With this tool, teams can perform passive network monitoring to keep track of sessions, hostnames, operating system, open ports, etc. without interfering with the network. It also identifies PCAP files for offline analysis. A highly intuitive user interface, faster processing, and open-source flexibility make NetworkMiner a popular tool among network administrators. You can learn more about the tool here.
8. Colasoft Caspa
Capsa is a simple network performance analysis and diagnostics tool, which can help you in real-time packet capturing and analysis. Its simple installation and a highly intuitive interface make it easier to implement. The application works on both LAN and WLAN networks and offers in-depth packet decoding. It offers a holistic view of the entire network, which helps administrators stay on top of their environment, detect issues, pinpoint the source of the error, and take remedial actions. The free version of the software can monitor up to 10 IP addresses but lacks several useful features. However, you’ll find the paid version highly useful for network security analysis.
Conclusion
We’ve discussed packet sniffing in detail and also covered some of the most popular packet sniffers used by IT teams around the world. Utilities like Tcpdump and Windump could be installed on all major platforms and support monitoring of network infrastructure. It’s possible to improve packet analysis further with tools like Wireshark. However, open-source tools can pose security and scalability challenges. For end-to-end monitoring of enterprise networks, system administrators have to rely on a wide range of monitoring techniques and tools. Installing open-source tools for every task can take up significant time and effort. This is why we recommend a commercial monitoring tools like SolarWinds Network Performance Monitor, which offers a free 30-day trial, so you can experience its multiple advanced features for comprehensive network analysis first hand.
